Secure.Compliant.Sovereign AI Empower Enterprise Data Sovereigntyand Governance
TWSC offers a secure and compliant one-stop AI outsourcing solution. With a multi-layered defense-in-depth mechanism and international certifications, we safeguard enterprises’ investments of AI adoption. Our commitment to guaranteed data sovereignty and privacy security ensures technical independence while enhancing market competitiveness.
Secure AI
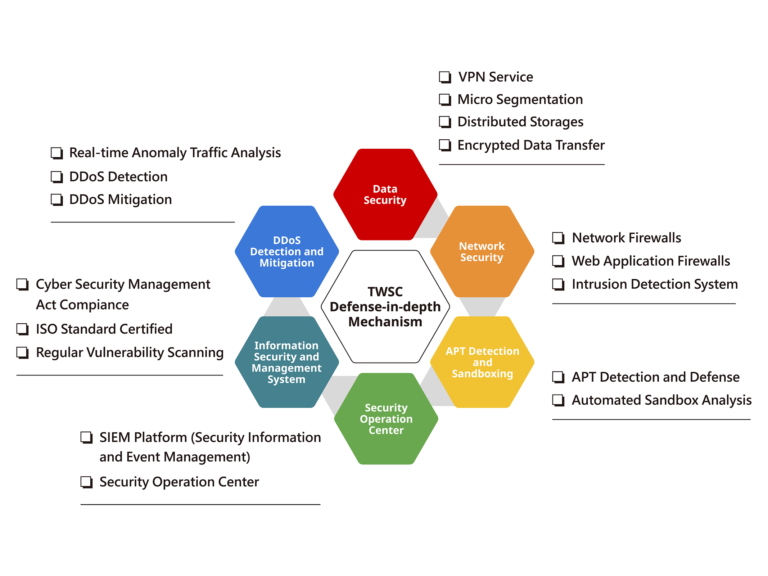
TWSC safeguards user data, models, and decision-making processes with a robust six-pillar security service. With protection at the management, physical security, and data levels, we offer a secure and reliable environment for users to build, run, and scale application development.
Compliant AI
TWSC is dedicated to delivering a secure and compliant AI environment by adhering to the highest cybersecurity standards. Our commitment includes Level A regulations and prestigious international certifications such as ISO, GDPR, HIPAA, and DCOS Level-4. Offered through enterprise-grade SLAs, our services ensure compliance with stringent regulatory requirements across industries.
Sovereign AI
TWSC provides a comprehensive generative AI outsourcing service that gives users full control over model selection, runtime environments, and fine-tuning content. By leveraging cloud and on-premises AI computing resources and collaborating with strategic partners on cybersecurity solutions, we enable our clients to focus on core competencies and drive innovation.
Secure AI : Integrating User and Organizational Data Protection and Privacy Assurance
Data Security
- Micro Segmentation:
Granular network isolation for enhanced security. - Distributed Storage Architecture:
High availability and data integrity. - Data Encryption:
Robust data protection through encryption.
Network Security
- Network Firewalls:
A high-performance solution that controls access and manages traffic across network and application layers to prevent unauthorized access. - Intrusion Detection System:
Enabling timely detection and mitigation of APT attacks through a centralized platform with real-time threat intelligence and incident response.
APT Detection and Sandboxing
- APT Detection:
Utilizes an automated behavioral analysis sandbox to detect and analyze malicious activities, including botnet and APT-related behaviors, ensuring proactive threat mitigation. - Integrated Security Operations Center:
Provides a centralized platform for real-time threat intelligence and incident response, enabling timely detection and mitigation of APT attacks.
Security Operation Center
- SIEM Platform Deployment:
Centralized log collection and correlation analysis from heterogeneous devices. - Security Operations Center:
24/7 threat monitoring, alerting, and rapid response.
Information Security and Management System
- Achieved multiple ISO international information security certifications: ISO 27001:2013 Information Security Management System, ISO 27017:2015 Cloud Services, and ISO 27018:2014 Cloud Privacy. We continuously enhance our internal security controls to support clients in establishing secure and manageable environments.
- Compliance with the Information Security Management Act: Certified as a Level A non-governmental organization, demonstrating our commitment to the highest information security standards.
DDoS Detection and Mitigation
- Real-time DDoS Protection:
Proactively observe, analyze, identify, and mitigate potential DDoS attacks using NetFlow data from edge routers. - Our solution employs advanced traffic scrubbing mechanisms to effectively mitigate the impact of DDoS attacks.
Compliant AI :
Infrastructure and platform services that meet international and governmental security and availability guidelines
Support market-demand security standards and certifications compliance, ensuring adherence to industry best practices
Professional Cybersecurity and High Assurance
High Security with International Standard Certifications
High Standards in Data Center Operations
SLAs and Service Commitments
High Protection with Two-Factor Authentication
Global







ISO 9001
ISO 27017
ISO 27018
ISO 50001
ISO 27001
ISO 20000
Taiwan


Other Countries


Sovereign AI :
Empowering users with customizable model selection, runtime environment configuration, and content fine-tuning
Collaborating with ecosystem partners to co-create comprehensive cybersecurity solutions, safeguarding user data and service security.
Choosing among diverse open-source and Chinese-optimized LLMs
Data is vital for enterprise operations and AI training. TWSC offers a growing suite of manageable, open-source models and FFM models optimized for Traditional Chinese operating in a secure, privacy-protected environment.
This empowers users to retain full ownership and control of their data assets, enhance data governance, and ensure security and compliance. With TWSC, enterprises can confidently develop and deploy generative AI applications, driving innovation and sustainable growth.